|
|
About
SecurityMgr.Info
& G2Online |
The mission of this site is to share SOPs and questions, especially for the non-Security Manager or Intelligence personnel who get thrown into an S2 (Military Security Manager) slot with no training. This will give you a system to ask questions, with out appearing the fool in front of your commander. We all have knowledge on a part of this business. If we share, we all look smart! This is done in conjunction with our list server S2_Online. Membership is open to all .mil and .gov addresses. Information may be found at: this LINK
Please bear with us because this website is in the process of being completely redone. Your links would be helpful.
I have retired from the military and a tour as civil service with the military, then looked at Homeland Security support from the intelligence community. And currently embarking on a tour with another Department. Any links or assistance you can provide would be appreciated, and may appear in the links at the bottom of this page.
All FREE Made Out of Individual's Dedication and Off Duty Time
|
| |

|
| |
|
All links
tested and
working on
10 Nov 2010
in Washington
DC. Please
report bad links
found on these
pages.
If you have
comments,
improvements, or
additional links
to add, please
email me! I look
forward to
hearing from
you! Many new
links are
constantly added
from readers
sending them to
me! We want this
site as
interactive and
user-friendly as
possible.

|
|
|
|
TIME MAG:
The Invasion of
the Chinese
Cyberspies, |
|
|
|
|
- "Hacker attacks in US linked to Chinese military", brietbart.com (retrieved 22 Apr 2008)
- Graham, B. "Hackers Attack Via Chinese Web Sites", Washington Post, August 25, 2005.
- Espiner, T. "Security experts lift lid on Chinese hack attacks", ZDNet News, November 23, 2005.
- Thornburgh, N. "Inside the Chinese Hack Attack", Time.com, August 25, 2005.
- Thornburgh, N. "The Invasion of the Chinese Cyberspies (And the Man Who Tried to Stop Them)", Time, August 29, 2005.
- Brenner, B. "Myfip's Titan Rain connection", SearchSecurity.com, August 31, 2005.
- Onley, D and Wait, P. "Red Storm Rising", Government Computing News, August 21, 2007
|
|
Operation Aurora |
|
Moonlight Maze |
|
Shawn Carpenter
a true American
Hero |
- NetWitness Corporation company website
- TIME Magazine (September 5, 2005 issue) article "The Invasion Of The Chinese Cyberspies (And the Man Who Tried to Stop Them)"
- TIME Magazine online (August 25, 2005) article "Inside the Chinese Hack Attack"
- Albuquerque Journal (September 15, 2005) "Battle Against Hackers Costs Employee Job"
- Albuquerque Journal (February 14, 2007) article "Sandia Hacker Gets $4 Million: Analyst Fired For FBI Contact"
- Computerworld (February 26, 2007) article "Q&A: Reverse Hacker Describes Ordeal"
- The New York Times (December 9, 2007) article "China Link Suspected in Lab Hacking"
- SecurityFocus (December 10, 2007) article "National Labs Hit With Targeted Attacks"
- ABC News (February 26, 2007) report "Jury Slaps Defense Giant for Neglecting National Security"
- TIME Magazine online (February 14, 2007) article "A Security Analyst Wins Big in Court"
- Federal Computer Weekly (February 26, 2007) article "Intercepts: Chinese Checkers"
- Congressional correspondence: Management cover-ups and malfeasance at Sandia (December 4, 2005) blog "LANL: The Real Story"
- The Register (February 16, 2007 article "Employee Fired For Probing Bad Guys Awarded $4.7M"
- Project on Government Oversight (POGO) (March 1, 2007) article "Cyber-security at Risk"
- Los Angeles Times (March 4, 2008) article "China's Computer Hacking Worries Pentagon"
- Computerworld (April 17, 2007) article "Reverse Hacker Case Gets Costlier for Sandia Labs"
- Forbes (September 11, 2007) article "Cyberspies Target Silent Victims"
- Computerworld (October 20, 2005) article "Guard Against Titan Rain Hackers"
- Searchsecurity.com (September 22, 2005) article "The Case of Shawn Carpenter: A Cautionary Tale"
- The Washington Times (July 26, 2007) article "FBI Calls Chinese Espionage 'Substantial'"
- Government Computer News (August 21, 2006) article "Red Storm Rising"
- Federal Computer Weekly (February 13, 2007) article "Cyber Officials: Chinese Hackers Attack 'Anything and Everything'"
- New Mexico State Judiciary Case Lookup System database "Carpenter vs. Sandia"
|
|
|
|
|
|
|
 S2_Online is
an email list server for qualified security
managers to help other new security managers.
This is shared brain power where we can ask for
assistance and leverage the the combined
experience of experienced Security Mgr · Click
here for S2_Online Email List Server (Formerly
Security Managers Info List Server)
S2_Online is
an email list server for qualified security
managers to help other new security managers.
This is shared brain power where we can ask for
assistance and leverage the the combined
experience of experienced Security Mgr · Click
here for S2_Online Email List Server (Formerly
Security Managers Info List Server) |
|
I often get the questions of is it G2 or
G-2. When I was growing up it was always
with a DASH. Now with the staff officers on
Blackberries, and the dash is time
consuming, most of us use no dash. |
The Director National Intelligence (DNI) has
an excellent electronic reading room which I
have linked at the bottom of this page.
Many Security Managers do not keep informed
about DNI changes.
|
|
|
S2's are
the Intelligence and Security Officer for
Military Units. This is often a thankless
job, where they receive little training. |
Office of the Director of National Intelligence
Electronic Reading Room
has the
Intelligence Community Directives (ICD) and Intelligence
Community Policy Guidance (ICPG).
Looking to start new
pages on new countries. Send me links, stories, &
pictures to use, I do credit donors!
Mexico
,
Philippines,
Thailand ,
Iran,
Iraq,
Korea
This site's Linguist and
Language
Page.

New OIF or IZ
or Iraq webpage started to enable TARGET SMART
deployers!
((Also new
IRAN Study
Word Doc) We have a
couple of tidbits from the Iraq page:
1.
English <-> Arabic basic phrases
for social, courtesy and
cooperation situations
2.
Examples (with translations) of typical
Arabic-language public signage & warning notices.

|
|
Upcoming Dates |
|
Computer Security - Virus Calendar
(Scroll down!!)
National
CounterTerrrorism Center
(NCTC)
NCTC Calendar

|
|

 |
The threat level in
the airline sector is
High or Orange.
Read more |
|
|
Spotlight |
|
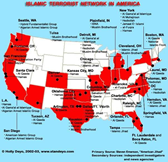
click to enlarge
CIA's World Fact Book
-
CIA Maps & Publications
|
|
|